Building Resilient Schools: The Role of Entry Screening in Security Protocols
The role of schools extends beyond merely disseminating knowledge. They're also crucial in nurturing and ensuring the safety and security...
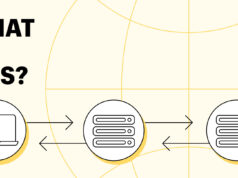
What Is DNS? A Complete Guide to How DNS Works
The Domain Name System (DNS) is the unsung hero in a world driven by digital connectivity, quietly enabling our seamless...
How Technology Has Altered Modern Gaming by Development of New Devices
Changes in technology have had an especially profound effect on the gaming industry. As a result of its recent success,...
Unlocking the Cloud Potential: The Benefits of IT Consulting Services in Cloud Computing
In our rapidly evolving digital world, businesses across the globe are embracing cloud computing, a powerful paradigm shift transforming the...
How to Choose the Right VPS Server for Your
In today's digital age, having a reliable and efficient web hosting solution is crucial for any business. A Virtual Private...
The Role of Artificial Intelligence in Online Gaming
Online gaming has become increasingly popular in recent years, with millions of people from all over the world participating in...
Bitcoin Gambling: 6 Tips for Protecting Your Funds & Personal Information
Back in the day, when gambling, the only important thing was to protect your money and win some. Today, things...
Tech-Driven Thrills: Unveiling the Intersection of Education, Entertainment, and Big Payout Casinos
The intersection of games and gambling has created a dynamic and captivating space that combines elements of both entertainment and...
How to Fix Corrupted MOV Files? Try These 5 Effective Methods!
MOV - a multimedia file format - was developed in 1998 by Apple Inc. The best thing about this video...
Security Service Edge (SSE) Explained: What is SSE?
The reliance on cloud-based applications, remote work, and interconnected devices is the new norm, and ensuring robust security has become...